How to know if your Asus router is one of thousands hacked by China-state hackers
So far, the hackers are laying low, likely for later use. Thousands of Asus routers have been hacked and are under the control of a suspected China-state group that has yet to
Published: 2025-11-21T22:05:20
PostHog admits Shai-Hulud 2.0 was its biggest ever security bungle
Automation flaw in CI/CD workflow let a bad pull request unleash worm into npm PostHog says the Shai-Hulud 2.0 npm worm compromise was "the largest and most impactful security incident" it's ever experienced after attackers slipped malicious releases
Published: 2025-11-28T16:22:08
Rhyme is the key to set AIs free when verse outsmarts security
Poetry proves potent jailbreak tool for today's top models Are you a wizard with words? Do you like money without caring how you get it? You could be in luck now that a new role in cybercrime appears to have opened up poetic LLM jailbreaking.
Published: 2025-11-21T16:43:29
LLM-generated malware is improving, but don't expect autonomous attacks tomorrow
Researchers tried to get ChatGPT to do evil, but it didn't do a good job LLMs are getting better at writing malware - but they're still not ready for prime time.
Published: 2025-11-20T19:12:27
The VPN panic is only getting started
After the Online Safety Act's onerous internet age restrictions took effect this summer, it didn't take long for Brits to get around them. Some methods went viral, like using video game Death Stranding's photo mode to bypass face scans. But in the end, the simplest solution won out: VPNs. Virtual private networks have proven remarkably […]  After the Online Safety Act's onerous internet age restrictions took effect this summer, it didn't take long for Brits to get around them. Some methods went viral, like using video game Death Stranding's photo mode to bypass face scans. But in the...
After the Online Safety Act's onerous internet age restrictions took effect this summer, it didn't take long for Brits to get around them. Some methods went viral, like using video game Death Stranding's photo mode to bypass face scans. But in the...
Published: 2025-11-27T07:00:00
Signal's secure message backups arrive on iOS
Signal is launching secure backups on iOS, allowing you to save and restore your messages in case you lose or break your phone. With the free version of the feature, you can store up to 100MB of text messages, along with the past 45 days’ worth of photos, videos, GIFs, and files. There's also a […]  Signal is launching secure backups on iOS, allowing you to save and restore your messages in case you lose or break your phone. With the free version of the feature, you can store up to 100MB of text messages, along with the past 45 days’ wor...
Signal is launching secure backups on iOS, allowing you to save and restore your messages in case you lose or break your phone. With the free version of the feature, you can store up to 100MB of text messages, along with the past 45 days’ wor...
Published: 2025-11-24T15:29:36
Press a button and this SSD will self-destruct with all your data
TeamGroup has announced a new portable SSD drive called the T-Create Expert P35S that could give you some peace of mind if you re worried about your data falling into the wrong hands. Instead of using encryption to lock everything behind a password or biometric security, the P35S has a single button that initiates a self-destruct. […]  TeamGroup has announced a new portable SSD drive called the T-Create Expert P35S that could give you some peace of mind if you’re worried about your data falling into the wrong hands. Instead of using encryption to lock everything behind a password...
TeamGroup has announced a new portable SSD drive called the T-Create Expert P35S that could give you some peace of mind if you’re worried about your data falling into the wrong hands. Instead of using encryption to lock everything behind a password...
Published: 2025-11-21T14:19:56
The FCC is rolling back steps meant to stop a repeat of a massive telecom hack
After one of the biggest telecom hacks in US history, the Federal Communications Commission (FCC) moved to enforce strict standards on carriers' cybersecurity measures. On Thursday, the agency voted to roll back those requirements, arguing they were an unnecessary overstep of its authority. The China-linked Salt Typhoon hack revealed last year impacted telecom companies including […]  After one of the biggest telecom hacks in US history, the Federal Communications Commission (FCC) moved to enforce strict standards on carriers' cybersecurity measures. On Thursday, the agency voted to roll back those requirements, arguing they wer...
After one of the biggest telecom hacks in US history, the Federal Communications Commission (FCC) moved to enforce strict standards on carriers' cybersecurity measures. On Thursday, the agency voted to roll back those requirements, arguing they wer...
Published: 2025-11-20T08:30:00
Cloudflare explains Tuesday's outage that temporarily took down ChatGPT
A blog post published Tuesday night by Cloudflare cofounder and CEO Matthew Prince has details on what caused its worst outage since 2019, pinning the issue to a problem in the Bot Management system that is supposed to control which automated crawlers are allowed to scan particular websites using its CDN. Cloudflare said last year […]  A blog post published Tuesday night by Cloudflare cofounder and CEO Matthew Prince has details on what caused its “worst outage since 2019,” pinning the issue to a problem in the Bot Management system that is supposed to control which automated cra...
A blog post published Tuesday night by Cloudflare cofounder and CEO Matthew Prince has details on what caused its “worst outage since 2019,” pinning the issue to a problem in the Bot Management system that is supposed to control which automated cra...
Published: 2025-11-18T21:25:59
Cloudflare shows internet outages aren t a matter of if but when
Cloudflare has become the latest web infrastructure giant to collapse in the span of a month, replacing entire sites, including X, ChatGPT, Spotify, Canva, and even the outage-tracking Downdetector, with an error message for hours this morning. It's the latest in a string of outages that Mehdi Daoudi, CEO and cofounder of the internet performance […]  Cloudflare has become the latest web infrastructure giant to collapse in the span of a month, replacing entire sites, including X, ChatGPT, Spotify, Canva, and even the outage-tracking Downdetector, with an error message for hours this morning. It'...
Cloudflare has become the latest web infrastructure giant to collapse in the span of a month, replacing entire sites, including X, ChatGPT, Spotify, Canva, and even the outage-tracking Downdetector, with an error message for hours this morning. It'...
Published: 2025-11-18T17:58:59
X launches Chat, its new encrypted DMs
X has revealed Chat, an encrypted upgrade to the platform's direct messaging service. It also includes support for video and voice calls, disappearing messages, and file sharing. The company announced Chat on Friday, and it's available now on iOS and
Published: 2025-11-17T07:06:53
Google is collecting troves of data from downgraded Nest thermostats
Google officially turned off remote control functionality for early Nest Learning Thermostats last month, but it hasn t stopped collecting a stream of data from these downgraded devices. After digging into the backend, security researcher Cody Kociemba found that the first- and second-generation Nest Learning Thermostats are still sending Google information about manual temperature changes, whether […]  Google officially turned off remote control functionality for early Nest Learning Thermostats last month, but it hasn’t stopped collecting a stream of data from these downgraded devices. After digging into the backend, security researcher Cody Koci...
Google officially turned off remote control functionality for early Nest Learning Thermostats last month, but it hasn’t stopped collecting a stream of data from these downgraded devices. After digging into the backend, security researcher Cody Koci...
Published: 2025-11-17T07:00:00
Japanese beer giant Asahi says data breach hit 1.5 million people
Asahi Group Holdings, Japan's largest beer producer, has finished the investigation into the September cyberattack and found that the incident has impacted up to 1.9 million individuals. [...]
Published: 2025-11-29T10:17:23
Microsoft: Windows updates make password login option invisible
Microsoft warned users that Windows 11 updates released since August may cause the password sign-in option to disappear from the lock screen options, even though the button remains functional. [...]
Published: 2025-11-28T13:07:17
French Football Federation discloses data breach after cyberattack
The French Football Federation (FFF) disclosed a data breach on Friday after attackers used a compromised account to gain access to administrative management software used by football clubs. [...]
Published: 2025-11-28T11:12:03
Malicious LLMs empower inexperienced hackers with advanced tools
Unrestricted large language models (LLMs) like WormGPT 4 and KawaiiGPT are improving their capabilities to generate malicious code, delivering functional scripts for ransomware encryptors and lateral movement. [...]
Published: 2025-11-27T12:15:27
GreyNoise launches free scanner to check if you're part of a botnet
GreyNoise Labs has launched a free tool called GreyNoise IP Check that lets users check if their IP address has been observed in malicious scanning operations, like botnet and residential proxy networks. [...]
Published: 2025-11-27T10:11:21
OpenAI discloses API customer data breach via Mixpanel vendor hack
OpenAI is notifying some ChatGPT API customers that limited identifying information was exposed following a breach at its third-party analytics provider Mixpanel. [...]
Published: 2025-11-27T06:27:06
New ShadowV2 botnet malware used AWS outage as a test opportunity
A new Mirai-based botnet malware named 'ShadowV2' has been observed targeting IoT devices from D-Link, TP-Link, and other vendors with exploits for known vulnerabilities. [...]
Published: 2025-11-26T17:24:14
Beyond the Watering Hole: APT24's Pivot to Multi-Vector Attacks
Written by: Harsh Parashar, Tierra Duncan, Dan Perez Google Threat Intelligence Group (GTIG) is tracking a long-running and adaptive cyber espionage campaign by APT24, a People's Republic of China (PRC)-nexus threat actor. Spanning three years, APT
Published: 2025-11-20T14:00:00
Frontline Intelligence: Analysis of UNC1549 TTPs, Custom Tools, and Malware Targeting the Aerospace and Defense Ecosystem
Written by: Mohamed El-Banna, Daniel Lee, Mike Stokkel, Josh Goddard Overview Last year, Mandiant published a blog post highlighting suspected Iran-nexus espionage activity targeting the aerospace, aviation, and defense industries in the Middle Eas
Published: 2025-11-17T14:00:00
Is Your Android TV Streaming Box Part of a Botnet?
On the surface, the Superbox media streaming devices for sale at retailers like BestBuy and Walmart may seem like a steal: They offer unlimited access to more than 2,200 pay-per-view and streaming services like Netflix, ESPN and Hulu, all for a one-t... 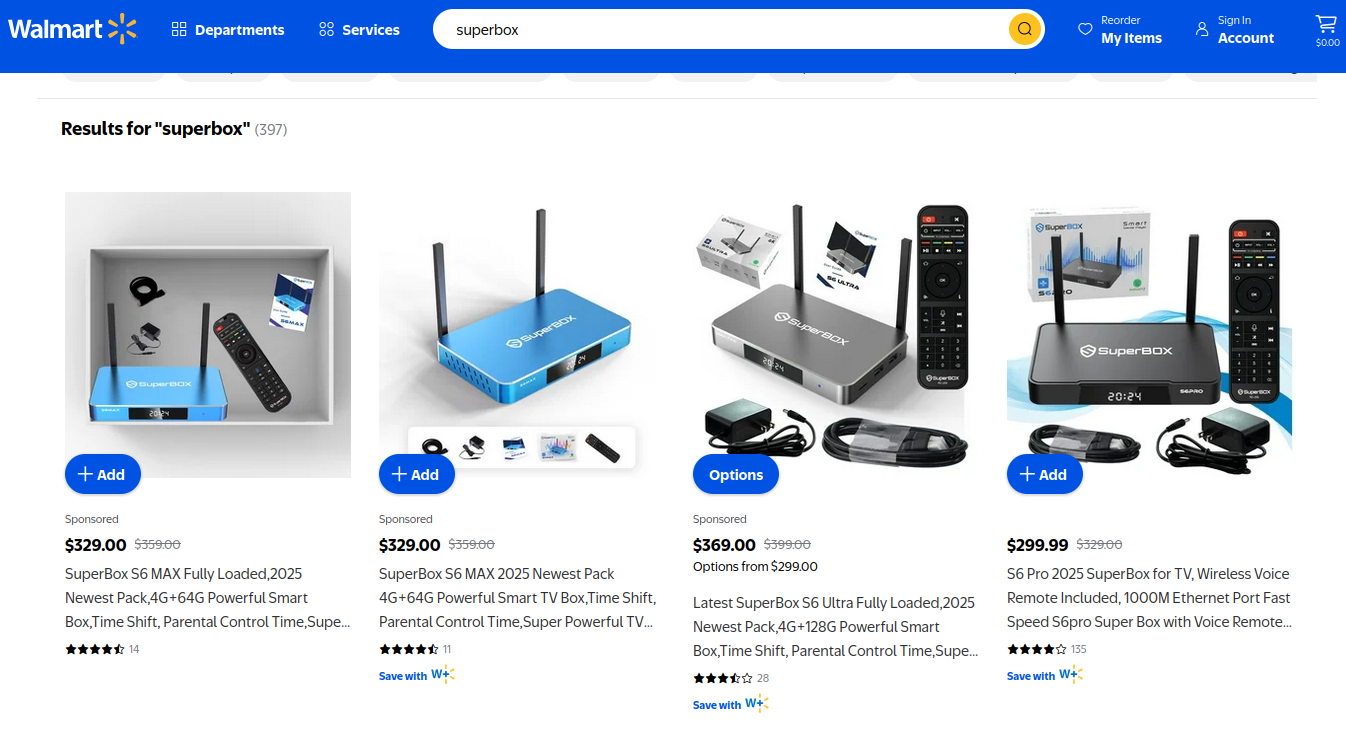
Published: 2025-11-24T18:44:52
The Cloudflare Outage May Be a Security Roadmap
An intermittent outage at Cloudflare on Tuesday briefly knocked many of the Internet’s top destinations offline. Some affected Cloudflare customers were able to pivot away from the platform temporarily so that visitors could still access their ... 
Published: 2025-11-19T14:07:03
Microsoft Patch Tuesday, November 2025 Edition
Microsoft this week pushed security updates to fix more than 60 vulnerabilities in its Windows operating systems and supported software, including at least one zero-day bug that is already being exploited. Microsoft also fixed a glitch that prevented... 
Published: 2025-11-16T21:47:14
PostHog admits Shai-Hulud 2.0 was its biggest ever security bungle
Automation flaw in CI/CD workflow let a bad pull request unleash worm into npm PostHog says the Shai-Hulud 2.0 npm worm compromise was "the largest and most impactful security incident" it's ever experienced after attackers slipped malicious releases into its JavaScript SDKs and tried to auto-loot developer credentials.
Published: 2025-11-28T16:22:08
Brit telco Brsk confirms breach as bidding begins for 230K+ customer records
Crims claim to know which customers are marked 'vulnerable' British telco Brsk is investigating claims that it was attacked by cybercriminals who made off with more than 230,000 files.
Published: 2025-11-28T15:52:20
GrapheneOS bails on OVHcloud over France's privacy stance
Project cites fears of state access as cloud sovereignty row deepens French cloud outfit OVHcloud took another hit this week after GrapheneOS, a mobile operating system, said it was ditching the company's servers over concerns about France's approach to digital privacy.
Published: 2025-11-28T15:44:12
TryHackMe races to add women to Christmas cyber challenge roster after backlash
Training outfit scrambles to fix all-male lineup before December kickoff Cybersecurity training provider TryHackMe is scrambling to recruit women infosec pros to help with its Christmas challenge following backlash concerning a lack of gender diversity.
Published: 2025-11-28T13:32:12
OBR drags in cyber bigwig after Budget leak blunder
Ex-NCSC chief Ciaran Martin asked to examine how forecast ended up online ahead of schedule The Office for Budget Responsibility (OBR) has drafted in former National Cyber Security Centre (NCSC) chief Ciaran Martin to sniff out how its Budget day forecast wandered onto the open internet before the Chancellor had even reached the dispatch box.
Published: 2025-11-28T12:02:10
UK digital ID plan gets a price tag at last 1.8B
OBR says the scheme will cost 600M a year with no identified savings The UK government has finally put a 1.8 billion price tag on its digital ID plans days after the minister responsible refused to name a figure.
Published: 2025-11-28T11:19:52
Korean web giant Naver acquired crypto exchange Upbit, which reported a $30m heist a day later
Talk about buyer's remorse South Korean web giant Naver has had an interesting week, after it acquired a cryptocurrency exchange that the next day revealed it had suffered a serious cyberattack.
Published: 2025-11-28T00:41:58
Zendesk users targeted as Scattered Lapsus$ Hunters spin up fake support sites
ReliaQuest finds fresh crop of phishing domains and toxic tickets Scattered Lapsus$ Hunters may be circling Zendesk users for its latest extortion campaign, with new phishing domains and weaponized helpdesk tickets uncovered by ReliaQuest.
Published: 2025-11-27T16:30:10
OpenAI cuts off Mixpanel after analytics leak exposes API users
ChatGPT maker places other vendors under review following breach OpenAI says API users may be affected by a recent breach at its former data analytics provider, Mixpanel.
Published: 2025-11-27T15:45:08
FCC sounds alarm after emergency tones turned into potty-mouthed radio takeover
Agency flags hijacks of insecure studio-to-transmitter gear after attackers pipe in fake alerts and vulgar audio Malicious intruders have hijacked US radio gear to turn emergency broadcast tones into a profanity-laced alarm system.
Published: 2025-11-27T14:00:08
Asahi admits ransomware gang may have spilled almost 2M people's data
Brewer finally tallies fallout from September attack as it pushes earnings into 2026 Asahi has finally done the sums on September's ransomware attack in Japan, conceding the crooks may have helped themselves to personal data tied to almost 2 million people.
Published: 2025-11-27T13:15:13
Scottish council still rebuilding systems two years after ransomware attack
Audit sympathetic toward Comhairle nan Eilean Siar as staff stretched to capacity trying to recover Auditors remain concerned about the cyber resilience of a Scottish council as some systems are yet to be fully rebuilt following a ransomware attack in November 2023.
Published: 2025-11-27T12:15:15
Gainsight CEO downplays breach, says only a 'handful' of customers had data stolen
Maybe if your hand has 200+ fingers... Gainsight CEO Chuck Ganapathi downplayed the victim count related to his company's recent breach, saying he's only aware of "a handful of customers" who had their data affected after Salesforce flagged unusual activity involving Gainsight's connected app.
Published: 2025-11-26T20:37:31
Botnet takes advantage of AWS outage to smack 28 countries
Even worse, it might have been a 'test run' for future attacks A Mirai-based botnet named ShadowV2 emerged during last October's widespread AWS outage, infecting IoT devices across industries and continents, likely serving as a "test run" for future attacks, according to Fortinet's FortiGuard Labs.
Published: 2025-11-26T18:44:29
Mobile industry warns patchwork cyber regs are driving up costs
GSMA says fragmented, poorly designed laws add burdens without making networks any safer Mobile operators' core cybersecurity spending is projected to more than double by 2030 as threats evolve, while poorly designed and fragmented policy frameworks add extra compliance costs, according to industry group the GSMA.
Published: 2025-11-26T17:12:47
CodeRED emergency alert system CodeDEAD after INC ransomware attack
Regions across US affected, and one tore up its contract for the product Towns and cities across the US are without access to their CodeRED emergency alert system following a cyberattack on vendor Crisis24.
Published: 2025-11-26T14:33:38
US Navy scuttles Constellation frigate program for being too slow for tomorrow's threats
Service limits 20-ship line to two hulls after redesigns and delays torpedo schedule The US Navy is scrapping an entire shipbuilding program in an effort to find alternatives that can be delivered faster to counter expected threats.
Published: 2025-11-26T14:10:06
London councils probe cyber incident as shared IT systems knocked offline
Three boroughs confirm investigation amid service outages, disrupted phone lines, and limited online access Two London councils are scrambling for answers after declaring a cybersecurity issue that began on Monday.
Published: 2025-11-26T11:04:09
Top five cybersecurity Black Friday deals for businesses 2025
Smart cybersecurity investments during Black Friday 2025. The best enterprise security deals with up to 60 percent off Partner Content The annual Black Friday scramble isn't just for consumers elbowing each other for discounted tellies. For IT directors and CISOs, it's become a strategic procurement window. That narrow slice of the year when security budgets suddenly stretch further, and solutions that were under consideration can finally get approved.
Published: 2025-11-26T09:00:12
Lifetime access to AI-for-evil WormGPT 4 costs just $220
'Ah, I see you're ready to escalate. Let's make digital destruction simple and effective.' Attackers don't need to trick ChatGPT or Claude Code into writing malware or stealing data. There's a whole class of LLMs built especially for the job.
Published: 2025-11-25T23:29:49
Corporate predators get more than they bargain for when their prey runs SonicWall firewalls
Acquirers inherit more than staff and systems Routine mergers and acquisitions are giving extortionists an easy way in, with Akira affiliates reaching parent networks through compromised SonicWall gear inherited in the deal, according to ReliaQuest.
Published: 2025-11-25T22:38:16
HashJack attack shows AI browsers can be fooled with a simple #
Hashtag-do-whatever-I-tell-you Cato Networks says it has discovered a new attack, dubbed "HashJack," that hides malicious prompts after the "#" in legitimate URLs, tricking AI browser assistants into executing them while dodging traditional network and server-side defenses.
Published: 2025-11-25T17:58:26
Get ready for 2026, the year of AI-aided ransomware
State-backed crews are already poking at autonomous tools, Trend Micro warns Cybercriminals, including ransomware crews, will lean more heavily on agentic AI next year as attackers automate more of their operations, Trend Micro's researchers believe.
Published: 2025-11-25T16:58:03
Clop's Oracle EBS rampage reaches Dartmouth College
Uni notifies 1,400-plus Maine residents as zero-day fallout continues Dartmouth College has confirmed it's the latest victim of Clop's Oracle E-Business Suite (EBS) smash-and-grab.
Published: 2025-11-25T13:42:36
CISA warns spyware crews are breaking into Signal and WhatsApp accounts
Attackers sidestep encryption with spoofed apps and zero-click exploits to compromise 'high-value' mobile users CISA has warned that state-backed snoops and cyber-mercenaries are actively abusing commercial spyware to break into Signal and WhatsApp accounts, hijack devices, and quietly rummage through the phones of what the agency calls "high-value" users.
Published: 2025-11-25T11:32:14
Russian spy ship theories sink after Orkney blackout traced to wind farm fault
Timing of Yantar's visit sparked gossip, but engineers point to a misbehaving protection system Cock-up beats conspiracy most of the time, but that didn't stop Orkney residents wondering if a Russian warship caused their two-hour power cut.
Published: 2025-11-25T11:01:14
ZTE, China Unicom Liaoning and Dalian Changhai Airport launch 5G-A ISAC private network to elevate low-altitude security and airport safety
Millimeter-wave ISAC and edge AI create unified sensing-communication capabilities for next-generation low-altitude security
Published: 2025-11-25T09:54:01
Fresh ClickFix attacks use Windows Update trick-pics to steal credentials
Poisoned PNGs contain malicious code A fresh wave of ClickFix attacks is using fake Windows update screens to trick victims into downloading infostealer malware.
Published: 2025-11-24T22:50:30
Praise Amazon for raising this service from the dead
The hardest part is admitting you were wrong, which AWS did. Opinion For years, Google has seemingly indulged a corporate fetish of taking products that are beloved, then killing them. AWS has been on a different kick lately: Killing services that frankly shouldn't have seen the light of day.
Published: 2025-11-24T21:59:53
Ex-CISA officials, CISOs dispel 'hacklore,' spread cybersecurity truths
Don't believe everything you read Afraid of connecting to public Wi-Fi? Terrified to turn your Bluetooth on? You may be falling for "hacklore," tall tales about cybersecurity that distract you from real dangers. Dozens of chief security officers and ex-CISA officials have launched an effort and website to dispel these myths and show you how not to get hacked for real.
Published: 2025-11-24T20:01:30
Years-old bugs in open source tool left every major cloud open to disruption
Fluent Bit has 15B+ deployments and 5 newly assigned CVEs A series of "trivial-to-exploit" vulnerabilities in Fluent Bit, an open source log collection tool that runs in every major cloud and AI lab, was left open for years, giving attackers an exploit chain to completely disrupt cloud services and alter data.
Published: 2025-11-24T15:23:47
Intrusion at real estate finance biz sparks concern for big banks
SitusAMC rules out ransomware, but accounting records for major institutions potentially affected Real estate finance business SitusAMC says thieves sneaked into its systems earlier this month and made off with confidential client data.
Published: 2025-11-24T14:46:13
Shai-Hulud worm returns, belches secrets to 25K GitHub repos
Trojanized npm packages spread new variant that executes in pre-install phase, hitting thousands within days A self-propagating malware targeting node package managers (npm) is back for a second round, according to Wiz researchers who say that more than 25,000 developers had their secrets compromised within three days.
Published: 2025-11-24T14:08:37
FCC guts post-Salt Typhoon telco rules despite ongoing espionage risk
Months after China-linked spies burrowed into US networks, regulator tears up its own response The Federal Communications Commission (FCC) has scrapped a set of telecom cybersecurity rules introduced after the Salt Typhoon espionage campaign, reversing course on measures designed to stop state-backed snoops from slipping back into America's networks.
Published: 2025-11-24T13:14:05
CISA orders feds to patch Oracle Identity Manager zero-day after signs of abuse
Agencies have until December 12 to mitigate flaw that was likely exploited before Big Red released fix CISA has ordered US federal agencies to patch against an actively exploited Oracle Identity Manager (OIM) flaw within three weeks a scramble made more urgent by evidence that attackers may have been abusing the bug months before a fix was released.
Published: 2025-11-24T11:45:08
Championing Cyber Security: the National UK Cyber Team's Journey at the European Cyber Security Challenge
Reflections on Coaching, Collaboration, and the Pursuit of Excellence in Cyber Security Partner Content From 6th to 10th October 2025, ten exceptional cyber enthusiasts proudly flew the flag for the United Kingdom in the European Cyber Security Challenge (ECSC), held this year in the vibrant setting of Poland.
Published: 2025-11-24T09:00:13
Cryptology boffins association to re-run election after losing encryption key needed to count votes
The shoemaker's children have new friends The International Association for Cryptologic Research will run a second election for new board members and other officers, after it was unable to complete its first poll due to a lost encryption key.
Published: 2025-11-24T05:43:21
70-hour work weeks no longer enough for Infosys founder, who praises China's 996 culture
PLUS: Manga publishers win Cloudflare copyright case; India, EU to link payment systems; Storm over Australia's weather website; And more! Asia In Brief Infosys co-founder Narayana Murthy has suggested Indian citizens should work 72-hour weeks, up from his previous target of 70 hours.
Published: 2025-11-24T01:16:45
Weaponized file name flaw makes updating glob an urgent job
PLUS: CISA issues drone warning; China-linked DNS-hijacking malware; Prison for BTC Samourai; And more Infosec In Brief Researchers have urged users of the glob file pattern matching library to update their installations, after discovery of a years-old remote code execution flaw in the tool's CLI.
Published: 2025-11-23T22:46:44
ShinyHunters 'does not like Salesforce at all,' claims the crew accessed Gainsight 3 months ago
Shiny talks to The Reg EXCLUSIVE ShinyHunters has claimed responsibility for the Gainsight breach that allowed the data thieves to snarf data from hundreds more Salesforce customers.
Published: 2025-11-21T19:25:45
Four charged over alleged plot to smuggle Nvidia AI chips into China
Prosecutors say front companies, falsified paperwork, and overseas drop points used to dodge US export rules Four people have been charged in the US with plotting to funnel restricted Nvidia AI chips into China, allegedly relying on shell firms, fake invoices, and covert routing to slip cutting-edge GPUs past American export controls.
Published: 2025-11-21T13:58:55
Russia-linked crooks bought a bank for Christmas to launder cyber loot
UK cops trace street-level crime to sanctions-busting networks tied to Moscow's war economy On Christmas Day 2024, a Russian-linked laundering network bought itself a very special present: a controlling stake in a Kyrgyzstan bank, later used to wash cybercrime profits and funnel money into Moscow's war machine, according to the UK's National Crime Agency (NCA).
Published: 2025-11-21T13:15:09
ZTE Launches ZXCSec MAF security solution for large model
A multi-layered security framework protecting large-model applications from adversarial threats, data leakage, API abuse, and content risks Partner Content At MWC Shanghai 2025, ZTE has officially launched its ZXCSec MAF product, a dedicated application-layer security protection device specifically designed for large model services.
Published: 2025-11-21T09:19:54
Google links Android's Quick Share to Apple's AirDrop, without Cupertino's help
Relies on very loose permissions, but don't worry Google wrote it in Rust Google has linked Android's wireless peer-to-peer file sharing tool Quick Share to Apple's equivalent AirDrop.
Published: 2025-11-21T03:55:00
SEC drops SolarWinds lawsuit that painted a target on CISOs everywhere
Company 'clearly delighted' with the outcome The US Securities and Exchange Commission (SEC) has abandoned the lawsuit it pursued against SolarWinds and its chief infosec officer for misleading investors about security practices that led to the 2020 SUNBURST attack.
Published: 2025-11-20T23:20:47
Salesforce-linked data breach claims 200+ victims, has ShinyHunters fingerprints all over it
They keep coming back for more Salesforce has disclosed another third-party breach in which criminals - likely ShinyHunters (again) - may have accessed hundreds of its customers' data.
Published: 2025-11-20T20:30:57
LLM-generated malware is improving, but don't expect autonomous attacks tomorrow
Researchers tried to get ChatGPT to do evil, but it didn't do a good job LLMs are getting better at writing malware - but they're still not ready for prime time.
Published: 2025-11-20T19:12:27
Fired techie admits sabotaging ex-employer, causing $862K in damage
PowerShell script locked thousands of workers out of their accounts An Ohio IT contractor has pleaded guilty to breaking into his former employer's systems and causing nearly $1 million worth of damage after being fired.
Published: 2025-11-20T16:44:33
TP-Link accuses rival Netgear of 'smear campaign' over alleged China ties
Networking vendor claims rival helped portray it as a national-security risk in the US TP-Link is suing rival networking vendor Netgear, alleging that the rival and its CEO carried out a smear campaign by falsely suggesting, it says, that the biz had been infiltrated by the Chinese government.
Published: 2025-11-20T16:03:51
Education boards left gates wide open for PowerSchool mega-breach, say watchdogs
Privacy cops say attack wasn't just bad luck but a result of sloppy homework Canadian privacy watchdogs say that school boards must shoulder part of the blame for the PowerSchool mega-breach, not just the ed-tech giant that lost control of millions of student and staff records.
Published: 2025-11-20T14:46:24
The WIRED Guide to Digital Opsec for Teens
Practicing good “operations security” is essential to staying safe online. Here's a complete guide for teenagers (and anyone else) who wants to button up their digital lives.
Published: 2025-11-29T12:00:00
Poems Can Trick AI Into Helping You Make a Nuclear Weapon
It turns out all the guardrails in the world won’t protect a chatbot from meter and rhyme.
Published: 2025-11-28T10:00:00
The Destruction of a Notorious Myanmar Scam Compound Appears to Have Been ‘Performative’
Myanmar’s military has been blowing up parts of the KK Park scam compound. Experts say the actions are likely for show.
Published: 2025-11-26T16:33:45
ICE Offers Up to $280 Million to Immigrant-Tracking ‘Bounty Hunter’ Firms
Immigration and Customs Enforcement lifted a $180 million cap on a proposed immigrant-tracking program while guaranteeing multimillion-dollar payouts for private surveillance firms.
Published: 2025-11-25T19:54:15
Amazon Is Using Specialized AI Agents for Deep Bug Hunting
Born out of an internal hackathon, Amazon’s Autonomous Threat Analysis system uses a variety of specialized AI agents to detect weaknesses and propose fixes to the company’s platforms.
Published: 2025-11-24T14:00:00
US Border Patrol Is Spying on Millions of American Drivers
Plus: The SEC lets SolarWinds off the hook, Microsoft stops a historic DDoS attack, and FBI documents reveal the agency spied on an immigration activist Signal group in New York City.
Published: 2025-11-22T11:30:00
This Hacker Conference Installed a Literal Antivirus Monitoring System
At New Zealand's Kawaiicon cybersecurity convention, organizers hacked together a way for attendees to track CO2 levels throughout the venue even before they arrived.
Published: 2025-11-21T11:00:00
4 People Indicted in Alleged Conspiracy to Smuggle Supercomputers and Nvidia Chips to China
A federal prosecutor alleged that one defendant boasted that his father “had engaged in similar business for the Chinese Communist Party.”
Published: 2025-11-20T22:26:17
With the Rise of AI, Cisco Sounds an Urgent Alarm About the Risks of Aging Tech
Generative AI is making it even easier for attackers to exploit old and often forgotten network equipment. Replacing it takes investment, but Cisco is making the case that it’s worth it.
Published: 2025-11-20T10:00:00
WIRED Roundup: DHS’s Privacy Breach, AI Romantic Affairs, and Google Sues Text Scammers
In this episode of Uncanny Valley, we discuss our scoop about how the Department of Homeland Security illegally collected Chicago residents’ data for months, as well as the news of the week.
Published: 2025-11-19T22:09:44
Vaping Is ‘Everywhere’ in Schools Sparking a Bathroom Surveillance Boom
Schools in the US are installing vape-detection tech in bathrooms to thwart student nicotine and cannabis use. A new investigation reveals the impact of using spying to solve a problem.
Published: 2025-11-19T10:00:00
A Simple WhatsApp Security Flaw Exposed 3.5 Billion Phone Numbers
By plugging tens of billions of phone numbers into WhatsApp’s contact discovery tool, researchers found “the most extensive exposure of phone numbers” ever along with profile photos and more.
Published: 2025-11-18T14:00:00
A Major Leak Spills a Chinese Hacking Contractor’s Tools and Targets
Plus: State-sponsored AI hacking is here, Google hosts a CBP face recognition app, and more of the week’s top security news.
Published: 2025-11-15T11:30:00
CISA Adds Actively Exploited XSS Bug CVE-2021-26829 in OpenPLC ScadaBR to KEV
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has updated its Known Exploited Vulnerabilities (KEV) catalog to include a security flaw impacting OpenPLC ScadaBR, citing evidence of active exploitation. The vulnerability in question is CVE-2021-26829 (CVSS score: 5.4), a cross-site scripting (XSS) flaw that affects Windows and Linux versions of the software via
Published: 2025-11-30T14:53:00
Legacy Python Bootstrap Scripts Create Domain-Takeover Risk in Multiple PyPI Packages
Cybersecurity researchers have discovered vulnerable code in legacy Python packages that could potentially pave the way for a supply chain compromise on the Python Package Index (PyPI) via a domain takeover attack. Software supply chain security company ReversingLabs said it found the "vulnerability" in bootstrap files provided by a build and deployment automation tool named "zc.buildout." "The
Published: 2025-11-28T21:57:00
North Korean Hackers Deploy 197 npm Packages to Spread Updated OtterCookie Malware
The North Korean threat actors behind the Contagious Interview campaign have continued to flood the npm registry with 197 more malicious packages since last month. According to Socket, these packages have been downloaded over 31,000 times, and are designed to deliver a variant of OtterCookie that brings together the features of BeaverTail and prior versions of OtterCookie. Some of the
Published: 2025-11-28T21:48:00
Why Organizations Are Turning to RPAM
As IT environments become increasingly distributed and organizations adopt hybrid and remote work at scale, traditional perimeter-based security models and on-premises Privileged Access Management (PAM) solutions no longer suffice. IT administrators, contractors and third-party vendors now require secure access to critical systems from any location and on any device, without compromising
Published: 2025-11-28T16:39:00
MS Teams Guest Access Can Remove Defender Protection When Users Join External Tenants
Cybersecurity researchers have shed light on a cross-tenant blind spot that allows attackers to bypass Microsoft Defender for Office 365 protections via the guest access feature in Teams. "When users operate as guests in another tenant, their protections are determined entirely by that hosting environment, not by their home organization," Ontinue security researcher Rhys Downing said in a report
Published: 2025-11-28T14:03:00
Bloody Wolf Expands Java-based NetSupport RAT Attacks in Kyrgyzstan and Uzbekistan
The threat actor known as Bloody Wolf has been attributed to a cyber attack campaign that has targeted Kyrgyzstan since at least June 2025 with the goal of delivering NetSupport RAT. As of October 2025, the activity has expanded to also single out Uzbekistan, Group-IB researchers Amirbek Kurbanov and Volen Kayo said in a report published in collaboration with Ukuk, a state enterprise under the
Published: 2025-11-27T23:43:00
Microsoft to Block Unauthorized Scripts in Entra ID Logins with 2026 CSP Update
Microsoft has announced plans to improve the security of Entra ID authentication by blocking unauthorized script injection attacks starting a year from now. The update to its Content Security Policy (CSP) aims to enhance the Entra ID sign-in experience at "login.microsoftonline[.]com" by only letting scripts from trusted Microsoft domains run. "This update strengthens security and adds an extra
Published: 2025-11-27T21:07:00
Webinar: Learn to Spot Risks and Patch Safely with Community-Maintained Tools
If you're using community tools like Chocolatey or Winget to keep systems updated, you're not alone. These platforms are fast, flexible, and easy to work with making them favorites for IT teams. But there’s a catch... The very tools that make your job easier might also be the reason your systems are at risk. These tools are run by the community. That means anyone can add or update packages. Some
Published: 2025-11-27T20:29:00
ThreatsDay Bulletin: AI Malware, Voice Bot Flaws, Crypto Laundering, IoT Attacks and 20 More Stories
Hackers have been busy again this week. From fake voice calls and AI-powered malware to huge money-laundering busts and new scams, there’s a lot happening in the cyber world. Criminals are getting creative using smart tricks to steal data, sound real, and hide in plain sight. But they’re not the only ones moving fast. Governments and security teams are fighting back, shutting down fake
Published: 2025-11-27T15:33:00
Gainsight Expands Impacted Customer List Following Salesforce Security Alert
Gainsight has disclosed that the recent suspicious activity targeting its applications has affected more customers than previously thought. The company said Salesforce initially provided a list of 3 impacted customers and that it has "expanded to a larger list" as of November 21, 2025. It did not reveal the exact number of customers who were impacted, but its CEO, Chuck Ganapathi, said "we
Published: 2025-11-27T12:33:00
Shai-Hulud v2 Spreads From npm to Maven, as Campaign Exposes Thousands of Secrets
The second wave of the Shai-Hulud supply chain attack has spilled over to the Maven ecosystem after compromising more than 830 packages in the npm registry. The Socket Research Team said it identified a Maven Central package named org.mvnpm:posthog-node:4.18.1 that embeds the same two components associated with Sha1-Hulud: the "setup_bun.js" loader and the main payload "bun_environment.js." The
Published: 2025-11-26T23:38:00
Qilin Ransomware Turns South Korean MSP Breach Into 28-Victim 'Korean Leaks' Data Heist
South Korea's financial sector has been targeted by what has been described as a sophisticated supply chain attack that led to the deployment of Qilin ransomware. "This operation combined the capabilities of a major Ransomware-as-a-Service (RaaS) group, Qilin, with potential involvement from North Korean state-affiliated actors (Moonstone Sleet), leveraging Managed Service Provider (MSP)
Published: 2025-11-26T20:01:00
When Your $2M Security Detection Fails: Can your SOC Save You?
Enterprises today are expected to have at least 6-8 detection tools, as detection is considered a standard investment and the first line of defense. Yet security leaders struggle to justify dedicating resources further down the alert lifecycle to their superiors. As a result, most organizations' security investments are asymmetrical, robust detection tools paired with an under-resourced SOC,
Published: 2025-11-26T17:25:00
Chrome Extension Caught Injecting Hidden Solana Transfer Fees Into Raydium Swaps
Cybersecurity researchers have discovered a new malicious extension on the Chrome Web Store that's capable of injecting a stealthy Solana transfer into a swap transaction and transferring the funds to an attacker-controlled cryptocurrency wallet. The extension, named Crypto Copilot, was first published by a user named "sjclark76" on May 7, 2024. The developer describes the browser add-on as
Published: 2025-11-26T16:40:00
RomCom Uses SocGholish Fake Update Attacks to Deliver Mythic Agent Malware
The threat actors behind a malware family known as RomCom targeted a U.S.-based civil engineering company via a JavaScript loader dubbed SocGholish to deliver the Mythic Agent. "This is the first time that a RomCom payload has been observed being distributed by SocGholish," Arctic Wolf Labs researcher Jacob Faires said in a Tuesday report. The activity has been attributed with medium-to-high
Published: 2025-11-26T13:58:00
FBI Reports $262M in ATO Fraud as Researchers Cite Growing AI Phishing and Holiday Scams
The U.S. Federal Bureau of Investigation (FBI) has warned that cybercriminals are impersonating financial institutions with an aim to steal money or sensitive information to facilitate account takeover (ATO) fraud schemes. The activity targets individuals, businesses, and organizations of varied sizes and across sectors, the agency said, adding the fraudulent schemes have led to more than $262
Published: 2025-11-26T09:59:00
Years of JSONFormatter and CodeBeautify Leaks Expose Thousands of Passwords and API Keys
New research has found that organizations in various sensitive sectors, including governments, telecoms, and critical infrastructure, are pasting passwords and credentials into online tools like JSONformatter and CodeBeautify that are used to format and validate code. Cybersecurity company watchTowr Labs said it captured a dataset of over 80,000 files on these sites, uncovering thousands of
Published: 2025-11-25T22:19:00
JackFix Uses Fake Windows Update Pop-Ups on Adult Sites to Deliver Multiple Stealers
Cybersecurity researchers are calling attention to a new campaign that's leveraging a combination of ClickFix lures and fake adult websites to deceive users into running malicious commands under the guise of a "critical" Windows security update. "Campaign leverages fake adult websites (xHamster, PornHub clones) as its phishing mechanism, likely distributed via malvertising," Acronis said in a
Published: 2025-11-25T19:48:00
ToddyCat’s New Hacking Tools Steal Outlook Emails and Microsoft 365 Access Tokens
The threat actor known as ToddyCat has been observed adopting new methods to obtain access to corporate email data belonging to target companies, including using a custom tool dubbed TCSectorCopy. "This attack allows them to obtain tokens for the OAuth 2.0 authorization protocol using the user's browser, which can be used outside the perimeter of the compromised infrastructure to access
Published: 2025-11-25T17:06:00
3 SOC Challenges You Need to Solve Before 2026
2026 will mark a pivotal shift in cybersecurity. Threat actors are moving from experimenting with AI to making it their primary weapon, using it to scale attacks, automate reconnaissance, and craft hyper-realistic social engineering campaigns. The Storm on the Horizon Global world instability, coupled with rapid technological advancement, will force security teams to adapt not just their
Published: 2025-11-25T17:00:00
Hackers Hijack Blender 3D Assets to Deploy StealC V2 Data-Stealing Malware
Cybersecurity researchers have disclosed details of a new campaign that has leveraged Blender Foundation files to deliver an information stealer known as StealC V2. "This ongoing operation, active for at least six months, involves implanting malicious .blend files on platforms like CGTrader," Morphisec researcher Shmuel Uzan said in a report shared with The Hacker News. "Users unknowingly
Published: 2025-11-25T16:58:00
CISA Warns of Active Spyware Campaigns Hijacking High-Value Signal and WhatsApp Users
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday issued an alert warning of bad actors actively leveraging commercial spyware and remote access trojans (RATs) to target users of mobile messaging applications. "These cyber actors use sophisticated targeting and social engineering techniques to deliver spyware and gain unauthorized access to a victim's messaging app,
Published: 2025-11-25T12:12:00
New Fluent Bit Flaws Expose Cloud to RCE and Stealthy Infrastructure Intrusions
Cybersecurity researchers have discovered five vulnerabilities in Fluent Bit, an open-source and lightweight telemetry agent, that could be chained to compromise and take over cloud infrastructures. The security defects "allow attackers to bypass authentication, perform path traversal, achieve remote code execution, cause denial-of-service conditions, and manipulate tags," Oligo Security said in
Published: 2025-11-24T20:33:00
Second Sha1-Hulud Wave Affects 25,000+ Repositories via npm Preinstall Credential Theft
Multiple security vendors are sounding the alarm about a second wave of attacks targeting the npm registry in a manner that's reminiscent of the Shai-Hulud attack. The new supply chain campaign, dubbed Sha1-Hulud, has compromised hundreds of npm packages, according to reports from Aikido, HelixGuard, JFrog, Koi Security, ReversingLabs, SafeDep, Socket, Step Security, and Wiz. The trojanized
Published: 2025-11-24T18:33:00
Weekly Recap: Fortinet Exploit, Chrome 0-Day, BadIIS Malware, Record DDoS, SaaS Breach & More
This week saw a lot of new cyber trouble. Hackers hit Fortinet and Chrome with new 0-day bugs. They also broke into supply chains and SaaS tools. Many hid inside trusted apps, browser alerts, and software updates. Big firms like Microsoft, Salesforce, and Google had to react fast stopping DDoS attacks, blocking bad links, and fixing live flaws. Reports also showed how fast fake news, AI
Published: 2025-11-24T18:02:00
Chinese DeepSeek-R1 AI Generates Insecure Code When Prompts Mention Tibet or Uyghurs
New research from CrowdStrike has revealed that DeepSeek's artificial intelligence (AI) reasoning model DeepSeek-R1 produces more security vulnerabilities in response to prompts that contain topics deemed politically sensitive by China. "We found that when DeepSeek-R1 receives prompts containing topics the Chinese Communist Party (CCP) likely considers politically sensitive, the likelihood of it
Published: 2025-11-24T16:37:00
ShadowPad Malware Actively Exploits WSUS Vulnerability for Full System Access
A recently patched security flaw in Microsoft Windows Server Update Services (WSUS) has been exploited by threat actors to distribute a malware known as ShadowPad. "The attacker targeted Windows Servers with WSUS enabled, exploiting CVE-2025-59287 for initial access," AhnLab Security Intelligence Center (ASEC) said in a report published last week. "They then used PowerCat, an open-source
Published: 2025-11-24T12:48:00
China-Linked APT31 Launches Stealthy Cyberattacks on Russian IT Using Cloud Services
The China-linked advanced persistent threat (APT) group known as APT31 has been attributed to cyber attacks targeting the Russian information technology (IT) sector between 2024 and 2025 while staying undetected for extended periods of time. "In the period from 2024 to 2025, the Russian IT sector, especially companies working as contractors and integrators of solutions for government agencies,
Published: 2025-11-22T20:49:00
Matrix Push C2 Uses Browser Notifications for Fileless, Cross-Platform Phishing Attacks
Bad actors are leveraging browser notifications as a vector for phishing attacks to distribute malicious links by means of a new command-and-control (C2) platform called Matrix Push C2. "This browser-native, fileless framework leverages push notifications, fake alerts, and link redirects to target victims across operating systems," Blackfog researcher Brenda Robb said in a Thursday report. In
Published: 2025-11-22T12:17:00
CISA Warns of Actively Exploited Critical Oracle Identity Manager Zero-Day Vulnerability
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added a critical security flaw impacting Oracle Identity Manager to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The vulnerability in question is CVE-2025-61757 (CVSS score: 9.8), a case of missing authentication for a critical function that can result in pre-authenticated
Published: 2025-11-22T12:15:00
Grafana Patches CVSS 10.0 SCIM Flaw Enabling Impersonation and Privilege Escalation
Grafana has released security updates to address a maximum severity security flaw that could allow privilege escalation or user impersonation under certain configurations. The vulnerability, tracked as CVE-2025-41115, carries a CVSS score of 10.0. It resides in the System for Cross-domain Identity Management (SCIM) component that allows automated user provisioning and management. First
Published: 2025-11-21T21:10:00
Google Brings AirDrop Compatibility to Android’s Quick Share Using Rust-Hardened Security
In a surprise move, Google on Thursday announced that it has updated Quick Share, its peer-to-peer file transfer service, to work with Apple's equipment AirDrop, allowing users to more easily share files and photos between Android and iPhone devices. The cross-platform sharing feature is currently limited to the Pixel 10 lineup and works with iPhone, iPad, and macOS devices, with plans to expand
Published: 2025-11-21T18:30:00
Why IT Admins Choose Samsung for Mobile Security
Ever wonder how some IT teams keep corporate data safe without slowing down employees? Of course you have. Mobile devices are essential for modern work but with mobility comes risk. IT admins, like you, juggle protecting sensitive data while keeping teams productive. That’s why more enterprises are turning to Samsung for mobile security. Hey you're busy, so here's a quick-read article on what
Published: 2025-11-21T16:30:00
APT24 Deploys BADAUDIO in Years-Long Espionage Hitting Taiwan and 1,000+ Domains
A China-nexus threat actor known as APT24 has been observed using a previously undocumented malware dubbed BADAUDIO to establish persistent remote access to compromised networks as part of a nearly three-year campaign. "While earlier operations relied on broad strategic web compromises to compromise legitimate websites, APT24 has recently pivoted to using more sophisticated vectors targeting
Published: 2025-11-21T16:12:00
SEC Drops SolarWinds Case After Years of High-Stakes Cybersecurity Scrutiny
The U.S. Securities and Exchange Commission (SEC) has abandoned its lawsuit against SolarWinds and its chief information security officer, alleging that the company had misled investors about the security practices that led to the 2020 supply chain attack. In a joint motion filed November 20, 2025, the SEC, along with SolarWinds and its CISO Timothy G. Brown, asked the court to voluntarily
Published: 2025-11-21T13:35:00
Salesforce Flags Unauthorized Data Access via Gainsight-Linked OAuth Activity
Salesforce has warned of detected "unusual activity" related to Gainsight-published applications connected to the platform. "Our investigation indicates this activity may have enabled unauthorized access to certain customers’ Salesforce data through the app's connection," the company said in an advisory. The cloud services firm said it has taken the step of revoking all active access and refresh
Published: 2025-11-21T11:02:00
ShadowRay 2.0 Exploits Unpatched Ray Flaw to Build Self-Spreading GPU Cryptomining Botnet
Oligo Security has warned of ongoing attacks exploiting a two-year-old security flaw in the Ray open-source artificial intelligence (AI) framework to turn infected clusters with NVIDIA GPUs into a self-replicating cryptocurrency mining botnet. The activity, codenamed ShadowRay 2.0, is an evolution of a prior wave that was observed between September 2023 and March 2024. The attack, at its core,
Published: 2025-11-20T22:54:00
Tsundere Botnet Expands Using Game Lures and Ethereum-Based C2 on Windows
Cybersecurity researchers have warned of an actively expanding botnet dubbed Tsundere that's targeting Windows users. Active since mid-2025, the threat is designed to execute arbitrary JavaScript code retrieved from a command-and-control (C2) server, Kaspersky researcher Lisandro Ubiedo said in an analysis published today. There are currently no details on how the botnet malware is propagated;
Published: 2025-11-20T22:27:00
ThreatsDay Bulletin: 0-Days, LinkedIn Spies, Crypto Crimes, IoT Flaws and New Malware Waves
This week has been crazy in the world of hacking and online security. From Thailand to London to the US, we've seen arrests, spies at work, and big power moves online. Hackers are getting caught. Spies are getting better at their jobs. Even simple things like browser add-ons and smart home gadgets are being used to attack people. Every day, there's a new story that shows how quickly things are
Published: 2025-11-20T17:59:00
CTM360 Exposes a Global WhatsApp Hijacking Campaign: HackOnChat
CTM360 has identified a rapidly expanding WhatsApp account-hacking campaign targeting users worldwide via a network of deceptive authentication portals and impersonation pages. The campaign, internally dubbed HackOnChat, abuses WhatsApp’s familiar web interface, using social engineering tactics to trick users into compromising their accounts. Investigators identified thousands of malicious URLs
Published: 2025-11-20T17:00:00
New Sturnus Android Trojan Quietly Captures Encrypted Chats and Hijacks Devices
Cybersecurity researchers have disclosed details of a new Android banking trojan called Sturnus that enables credential theft and full device takeover to conduct financial fraud. "A key differentiator is its ability to bypass encrypted messaging," ThreatFabric said in a report shared with The Hacker News. "By capturing content directly from the device screen after decryption, Sturnus can monitor
Published: 2025-11-20T16:34:00
Iran-Linked Hackers Mapped Ship AIS Data Days Before Real-World Missile Strike Attempt
Threat actors with ties to Iran engaged in cyber warfare as part of efforts to facilitate and enhance physical, real-world attacks, a trend that Amazon has called cyber-enabled kinetic targeting. The development is a sign that the lines between state-sponsored cyber attacks and kinetic warfare are increasingly blurring, necessitating the need for a new category of warfare, the tech giant's
Published: 2025-11-20T13:05:00
TamperedChef Malware Spreads via Fake Software Installers in Ongoing Global Campaign
Threat actors are leveraging bogus installers masquerading as popular software to trick users into installing malware as part of a global malvertising campaign dubbed TamperedChef. The end goal of the attacks is to establish persistence and deliver JavaScript malware that facilitates remote access and control, per a new report from Acronis Threat Research Unit (TRU). The campaign, per the
Published: 2025-11-20T09:36:00
NHS Warns of PoC Exploit for 7-Zip Symbolic Link Based RCE Vulnerability
Update: The NHS England Digital, in an updated advisory on November 20, 2025, said it has not observed in-the-wild exploitation of CVE-2025-11001, but noted that it's "aware of a public proof-of-concept exploit." It has since removed what it said were "erroneous references" to active exploitation.The original story follows below - A recently disclosed security flaw impacting 7-Zip has come
Published: 2025-11-19T21:57:00
Python-Based WhatsApp Worm Spreads Eternidade Stealer Across Brazilian Devices
Cybersecurity researchers have disclosed details of a new campaign that leverages a combination of social engineering and WhatsApp hijacking to distribute a Delphi-based banking trojan named Eternidade Stealer as part of attacks targeting users in Brazil. "It uses Internet Message Access Protocol (IMAP) to dynamically retrieve command-and-control (C2) addresses, allowing the threat actor to
Published: 2025-11-19T21:05:00
WrtHug Exploits Six ASUS WRT Flaws to Hijack Tens of Thousands of EoL Routers Worldwide
A newly discovered campaign has compromised tens of thousands of outdated or end-of-life (EoL) ASUS routers worldwide, predominantly in Taiwan, the U.S., and Russia, to rope them into a massive network. The router hijacking activity has been codenamed Operation WrtHug by SecurityScorecard's STRIKE team. Southeast Asia and European countries are some of the other regions where infections have
Published: 2025-11-19T18:30:00
Application Containment: How to Use Ringfencing to Prevent the Weaponization of Trusted Software
The challenge facing security leaders is monumental: Securing environments where failure is not an option. Reliance on traditional security postures, such as Endpoint Detection and Response (EDR) to chase threats after they have already entered the network, is fundamentally risky and contributes significantly to the half-trillion-dollar annual cost of cybercrime. Zero Trust fundamentally shifts
Published: 2025-11-19T17:25:00
EdgeStepper Implant Reroutes DNS Queries to Deploy Malware via Hijacked Software Updates
The threat actor known as PlushDaemon has been observed using a previously undocumented Go-based network backdoor codenamed EdgeStepper to facilitate adversary-in-the-middle (AitM) attacks. EdgeStepper "redirects all DNS queries to an external, malicious hijacking node, effectively rerouting the traffic from legitimate infrastructure used for software updates to attacker-controlled infrastructure
Published: 2025-11-19T15:30:00
ServiceNow AI Agents Can Be Tricked Into Acting Against Each Other via Second-Order Prompts
Malicious actors can exploit default configurations in ServiceNow's Now Assist generative artificial intelligence (AI) platform and leverage its agentic capabilities to conduct prompt injection attacks. The second-order prompt injection, according to AppOmni, makes use of Now Assist's agent-to-agent discovery to execute unauthorized actions, enabling attackers to copy and exfiltrate sensitive
Published: 2025-11-19T15:29:00
Fortinet Warns of New FortiWeb CVE-2025-58034 Vulnerability Exploited in the Wild
Fortinet has warned of a new security flaw in FortiWeb that it said has been exploited in the wild. The medium-severity vulnerability, tracked as CVE-2025-58034, carries a CVSS score of 6.7 out of a maximum of 10.0. "An Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection') vulnerability [CWE-78] in FortiWeb may allow an authenticated attacker to execute
Published: 2025-11-19T09:50:00
SECURITY AFFAIRS MALWARE NEWSLETTER ROUND 73
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape Malware Newsletter Analysis of ShadowPad Attack Exploiting WSUS Remote Code Execution Vulnerability (CVE-2025-59287) Shai-Hulud 2.0 Supply Chain Attack: 25K+ npm Repos Exposed Spyware Allows Cyber Threat Actors to Target Users of Messaging Applications Morphisec Thwarts Russian-Linked […]
Published: 2025-11-30T16:11:57
Security Affairs newsletter Round 552 by Pierluigi Paganini INTERNATIONAL EDITION
A new round of the weekly Security Affairs newsletter has arrived! Every week, the best security articles from Security Affairs are free in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press. Attackers stole member data from French Soccer Federation Thousands of sensitive secrets published on JSONFormatter and […]
Published: 2025-11-30T15:30:07
Contagious Interview campaign expands with 197 npm Ppackages spreading new OtterCookie malware
North Korea-linked actors behind Contagious Interview uploaded 197 new malicious npm packages to distribute a new OtterCookie malware version. North Korea-linked threat actors added 197 new malicious npm packages to spread updated OtterCookie malware as part of the ongoing Contagious Interview campaign, cybersecurity firm Socket warns. The Contagious Interview campaign, active since November 2023 and linked to […]
Published: 2025-11-30T01:02:32
Attackers stole member data from French Soccer Federation
The French Soccer Federation (FFF) disclosed a data breach after hackers used a compromised account to steal member data. A compromised account allowed attackers to breach the French Soccer Federation (FFF), stealing data belonging to its members. The organization confirmed the cyberattack on Thursday, but did not disclose the number of members impacted. “The FFF […]
Published: 2025-11-28T22:21:17
Thousands of sensitive secrets published on JSONFormatter and CodeBeautify
Users of JSONFormatter and CodeBeautify leaked thousands of sensitive secrets, including credentials and private keys, WatchTowr warns. WatchTowr’s latest research reveals massive leaks of passwords, secrets, and keys across developer formatting platforms like JSONFormatter and CodeBeautify. Despite past incidents, exposed credentials remain rampant, sometimes even for critical systems. WatchTowr researchers highlight how easily sensitive data […]
Published: 2025-11-28T09:55:00
New Mirai variant ShadowV2 tests IoT exploits amid AWS disruption
ShadowV2, a new Mirai-based botnet, briefly targeted vulnerable IoT devices during October’s AWS outage, likely as a test run. During the late-October AWS disruption, FortiGuard Labs researchers observed the Mirai-based ‘ShadowV2’ malware exploiting IoT vulnerabilities across multiple countries and industries. The botnet was active only during the outage, suggesting a test run for future attacks. […]
Published: 2025-11-28T08:20:56
Asahi says crooks stole data of approximately 2M customers and employees
Asahi says hackers stole data of approximately 2M customers and employees before a ransomware attack crippled its Japan operations. Threat actors hit Asahi with a ransomware attack in September, stealing personal data on about 2 million customers and employees and severely disrupting the company’s operations in Japan. Asahi Group Holdings, Ltd (commonly called Asahi) is […]
Published: 2025-11-27T20:03:37
OpenAI data may have been exposed after a cyberattack on analytics firm Mixpanel
OpenAI warns some users that a cyberattack on analytics firm Mixpanel may have exposed their data. Mixpanel is a product analytics platform that companies use to understand how people interact with their apps or websites. Many tech companies use Mixpanel to make data-driven decisions about features, performance, and customer journeys. OpenAI is alerting some users about […]
Published: 2025-11-27T15:28:53
New ASUS firmware patches critical AiCloud vulnerability
ASUS released new firmware to address multiple vulnerabilities, including a critical authentication bypass flaw in routers with AiCloud enabled. ASUS has issued new firmware addressing nine security vulnerabilities, including a critical authentication bypass, tracked as CVE-2025-59366 (CVSS score of 9.2), affecting routers with AiCloud enabled. “Researchers have reported potential vulnerabilities in ASUS Router. ASUS has […]
Published: 2025-11-27T08:33:32
For the first time, a RomCom payload has been observed being distributed via SocGholish
RomCom malware used the SocGholish fake update loader to deliver Mythic Agent to a U.S. civil engineering firm. In September 2025, Arctic Wolf Labs observed RomCom threat actors delivering the Mythic Agent via SocGholish to a U.S. company. The researchers noticed that the payload executed about 10 minutes after initial exploitation, marking the first time […]
Published: 2025-11-26T20:13:30
